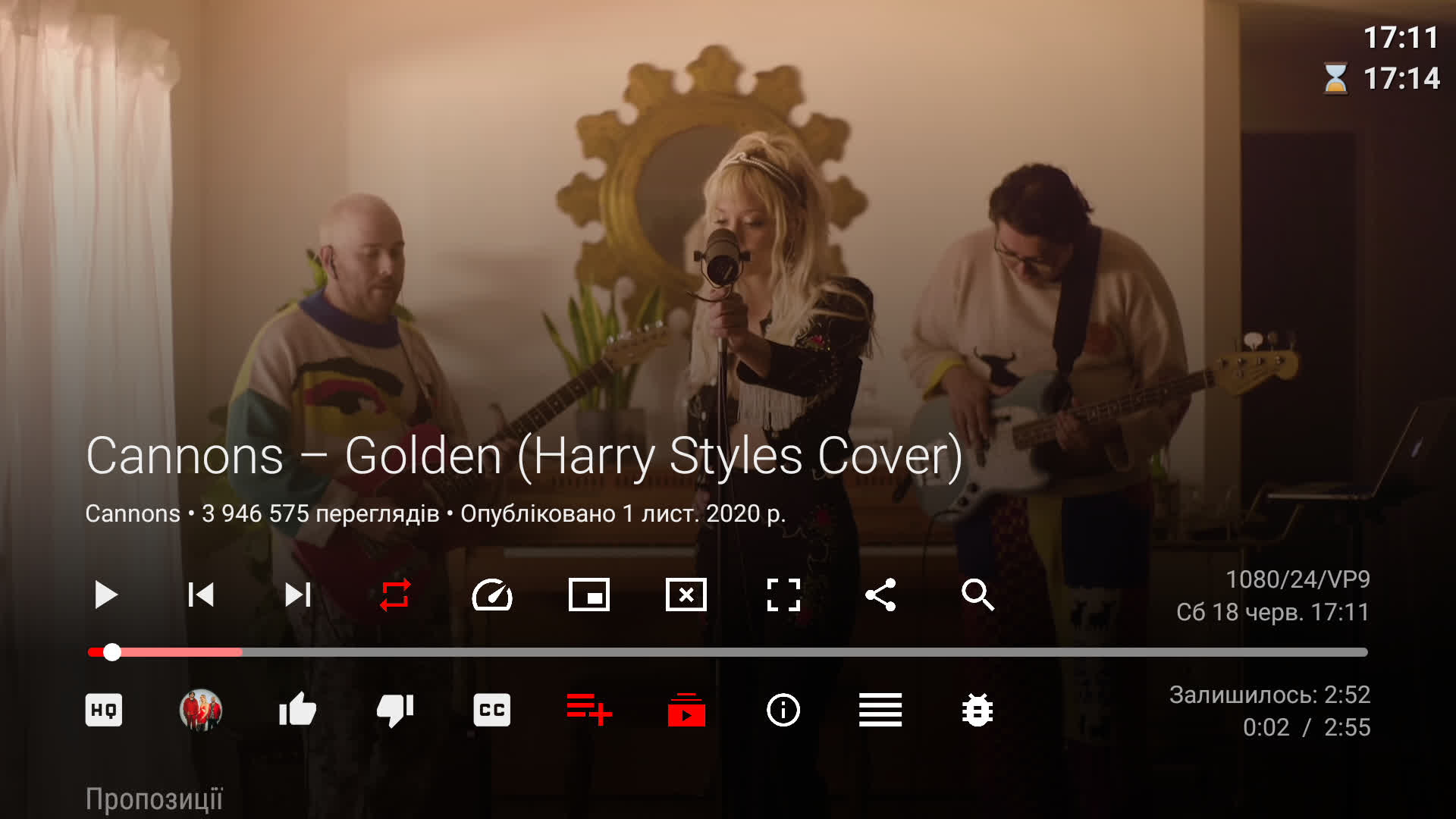
Facepalm: SmartTube is a popular alternative media player for watching YouTube and other streaming sources on Android TV, usually with the benefit of removing ads. Unfortunately, the open-source app has recently become a potential security risk after the developer's computer was infected with malware.
According to recent user reports, Google Play Protect disabled SmartTube after detecting suspicious behavior. Android's anti-malware service flagged the app as a "fake" tool designed to take over devices or steal user data. The SmartTube developer later confirmed what actually happened behind the scenes.
The dev announced that his digital signature had allegedly been compromised, making subsequent updates potentially unsafe. The signature could have been misused to publish a counterfeit version of the app under his name, prompting him to abandon the old signature entirely and switch to a new one.
However, changing the signature also required changing the app's identifier, Yuriy L said. As a result, the original app is now effectively abandoned, and users must install the new version to continue receiving security updates. A third-party developer later analyzed the SmartTube release that Google Play Protect disabled (version 30.51), uncovering suspicious behavior for what should have been a simple media player.
The compromised release contained a hidden library named libalphasdk.so, which was designed to contact a third-party server whenever SmartTube launched.
The library also collected a significant amount of device data, including the Android version, network operator, network type (Wi-Fi or mobile data), and more. Finally, it allowed the app to receive further instructions from the internet without any user prompt or control.
How did cybercriminals manage to compromise the SmartTube developer's signature and inject their own malicious library? According to Yuriy L, the computer he used to compile the APK archives before uploading them to GitHub had been infected with malware. This was likely the reason certain SmartTube versions were flagged by Google Play Protect and other anti-malware services.
The infected PC has since been wiped, and the new digital signature should make the latest SmartTube release safe to use again. However, users who installed one of the compromised versions are now essentially on their own, the old app will no longer receive updates... but most importantly you should delete it from your devices.
The incident underscores the precarious state of app security and development within the Android ecosystem. Google recently came under fire for making sideloading outside the Play Store significantly more difficult, requiring developers to verify their identity in a centralized database. But if a developer's signature is compromised, stricter sideloading rules won't stop a malicious update from reaching users' devices – despite Google's claims about the "improved" security the new policy will provide.